A security researcher announced today a vulnerability in the Wi-Fi Protected Access 2 (WPA2) protocol. The vulnerability, nicknamed "Krack Attack," exploits the design of the protocol to decrypt data previously assumed to be safe such as credit card numbers and login information. What is actually going on? Are you safe? What should you do?
A security researcher announced today a vulnerability in the Wi-Fi Protected Access 2 (WPA2) protocol. The vulnerability, nicknamed "Krack Attack," exploits the design of the protocol to decrypt data previously assumed to be safe such as credit card numbers and login information. What is actually going on? Are you safe? What should you do?
The Krack Attack in simple English
This is a variation on the "rogue wireless network" attack, which is a kind of "man in the middle" attack. An attacker creates a "fake" wireless network with the same name as the legitimate network, and forces the "client" (your laptop, tablet, or smartphone) to reset the encryption key. Once that is done, your laptop will send information to this new, fake network. Whomever controls that network can see any unencrypted data transmitted over it. The person who discovered this flaw notes that it is particularly "catastrophic" against Android and Linux devices.
Is Krack Attack really a big deal?
This attack is, in practice, very complicated. With the disclosure of this WPA2 vulnerability, the attack may become more widespread over time. For now, actually encountering this attack in the wild (including at your association or nonprofit) is very unlikely. Furthermore, any traffic going over proper TLS encryption will not be visible even to a "man in the middle" attack like this one. There is no need to panic—at this point.
What should associations and nonprofits do right now?
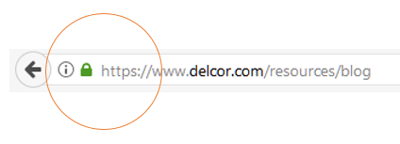 Traffic that is properly encrypted is not visible—even if you are on a rogue network. To ensure your protection, only use websites that are properly configured with HTTPS—you should do this anyway! Never, ever log in or enter sensitive info on a website that is not properly secured (look for the closed padlock in your browser's location bar). You should also be on the lookout for news from your smartphone, laptop, and other mobile device vendors for any patches they may release—and follow their instructions to install necessary updates. If further action becomes necessary and you outsource your IT support, your managed services provider (MSP) should advise you on next steps.
Traffic that is properly encrypted is not visible—even if you are on a rogue network. To ensure your protection, only use websites that are properly configured with HTTPS—you should do this anyway! Never, ever log in or enter sensitive info on a website that is not properly secured (look for the closed padlock in your browser's location bar). You should also be on the lookout for news from your smartphone, laptop, and other mobile device vendors for any patches they may release—and follow their instructions to install necessary updates. If further action becomes necessary and you outsource your IT support, your managed services provider (MSP) should advise you on next steps.
Data hacks, and the methods criminals use to retrieve your data, are proliferating. Be wary—your association or nonprofit is not immune. What should you be protecting your organization against? Download our free ebook, The Cybersecurity Watchlist for Association & Nonprofit CEOs, to find out.