How times have changed. A few years ago, server rooms in associations were crammed full of equipment. Now, they’ve emptied out as associations have moved to the cloud. Will those same rooms soon contain bitcoin miners?
As quickly and pervasively as ransomware is spreading, nothing would surprise us, seeing as you need bitcoins to pay ransom. Unfortunately, many associations are going to find themselves paying that ransom, unless they take our advice:
Protect Your Organization Against Ransomware Exploits
How ransomware gets in
Ransomware infiltrates networks thanks to simple human error—the type of errors anyone can easily make, especially when rushed or distracted.
The most common entry-point is phishing emails that appear legit. They look like they’re from a company you trust (FedEx, Apple, Google) or a person your know (your CEO or colleague). The hacker wants to trick you into opening an attachment infected by ransomware or clicking on a link to an infected site. If you’re not careful, it works, and the hacker’s job is done.
When you land on a compromised website where malicious code has been inserted in content or images, ransomware is automatically downloaded to your computer.
Another common source is malvertising. Online advertising networks mistakenly publish ads containing malware on sites with large audiences. Google, New York Times, BBC, and Newsweek have all unknowingly hosted malvertising.
Hackers also use bots to seek vulnerabilities. For example, they’ll search servers for accounts you might have forgotten about, like “temp” or “scanner,” with weak passwords. Once they get in, they infect that server with ransomware and wait for it to spread.
How ransomware works
Once someone opens an attachment or clicks a bad link, ransomware starts encrypting files on the infected PC’s local hard drive. You need to remove the infected machine from the network immediately, or the ransomware won’t get caught in time and will spread like wildfire. It will spawn multiple infection threads that attach themselves to network drives. The ransomware ends up on your servers and encrypts everything.
How to recover from a ransomware attack
What do you do if your association is attacked by ransomware? When it happens, everything’s locked down and everyone’s locked out. Ideally, you restore files from backup. The time and effort involved in restoration depends on several factors:
- How thorough and comprehensive are your backups?
- How recent are they?
- What type of backups do you have? Pro tip: If you’re using shadow copy backup software, it will help you recover more quickly than having to rely on a system-wide backup.
- Do you know if your restoration process works? Has it been tested recently?
Plan A: ignore and restore
If your backups are complete and current, your organization can ignore the ransom notice and begin to restore your data. Restoration could take anywhere from 15 minutes to several days depending on how far the encryption spread, how many accounts and permissions the original victim had access to, and how large of a data set needs restoring. For example, if your on-premise web server gets encrypted, your website goes down. And if your general ledger gets encrypted, ouch.
Plan B: pay the ransom
Cybercriminals win when you pay the ransom, so don’t put your association (and your board) in this position. But, if you don’t have good backups, you may have no other choice. Do you really want to opt for Plan B?
Here’s how it works.
Ransoms are brokered in bitcoin—a cryptocurrency used for many legitimate means but also adopted by the black market. Since they’re not traceable, they’re not so easy to buy with your credit card. You have the choice of providing your bank account information to these criminals (bad idea), trying to find someone who’s willing to sell you bitcoins, or setting up a virtual wallet to buy bitcoins.
When hackers cast a wide net rather than a targeted attack, ransom is typically 1 to 4 bitcoins. The value of bitcoins is soaring. For example, back in April, a bitcoin cost $1,338. By mid-May, it had risen to $1,800. Now, one bitcoin costs $2,563—nearly double what it cost just two months ago! At that rate, a ransomware attack today could cost you up to $10,000.
The business costs hurt more than the $10,000 hit to your budget. While waiting 3-5 business days to set up the virtual wallet, your staff are locked out of their files. Work comes to a standstill. You can’t fulfill member services. Your board is likely irate.
How to avoid becoming a ransomware victim
Your IT department alone can’t protect your organization from ransomware. They’ll do their best to maintain a perimeter defense and fix any security vulnerabilities in your network. But, they can’t watch over every employee’s shoulder to make sure staff don’t open or click something they shouldn’t.
In a security survey released this year, 80% of the respondents said “carelessness and failure to implement and install security on their BYOD and mobile devices” was more dangerous than targeted hacks and rogue code.
Security is everyone’s responsibility—from the CEO down. Everyone needs to be educated on how to spot and prevent ransomware, email spoofing, and other phishing attempts.
We recommend using a security awareness training program like KnowBe4 to test your staff’s susceptibility to getting phished. If someone falls for a pseudo-phishing attempt, they are asked to take self-paced training modules. New hires should also go through these training modules, and you should consider recurring training for all employees. Staff must know it’s their responsibility to protect themselves and the organization.
The C-suite must take the initiative to build a security-aware culture. Budget for staff training. Reach out to your Managed Services Provider or security consultant to do a periodic assessment. Build these assessments into your operational plan and budget.
How ransomware impacts your organization
You may find your auditors are one step ahead of you. They almost always have a one-pager for the IT department requesting information about access and policies. They need to know whether your organization has security vulnerabilities that can put it at financial and legal risk.
Security breaches have legal ramifications. If you don’t exercise reasonable judgement in protecting the data in your care, your organization can theoretically be held in violation of regulations like PCI and HIPPA. Your organization and board have the legal and fiduciary duty to protect that information. Security breaches have job ramifications, too—as many CEOs learn too late.
How times have changed: ransomware then and now
Associations now reside in a much different security landscape than just a few years ago. In the old days, as long as no one hated you and you weren’t on the radar of troublemakers, you didn’t have to worry. Now, ransomware is automated, inexpensive, and pervasive. Cybercriminals bank on the fact that many organizations won’t have the proper defense or backups and will be more willing to shell out a few thousand dollars to get their files back than go through the hassle of restoring backups.
The old defensive approach is no longer sufficient. Along with solid backup practices, your organization must have a proactive, security-aware culture to protect it and your constituents from cybercriminals and ransomware. Find out if your organization is prepared to fend off the next wave of ransomware by reading our ebook, The Cybersecurity Watchlist for Association and Nonprofit Executives.
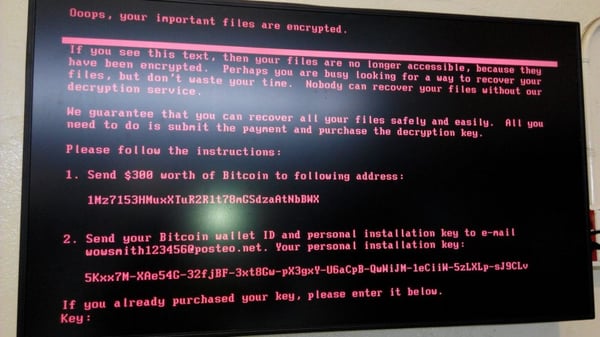
Petya / NotPetya / Petya-Variant / Goldeneye
While we were writing this post, a new attack hit on a global scale, making our advice even more timely and imperative. Familiarize yourself with this attack (and others like it—remember WannaCry?) so it doesn't happen to you.
Here's the latest news on Petya / NotPetya / Petya-Variant from around the web:
June 28, 2017
- NPR: Petya Ransomware Hits At Least 65 Countries; Microsoft Traces It To Tax Software
- The Guardian: ‘Petya’ ransomware attack: what is it and how can it be stopped?
- The Sun: Petya Goldeneye ransomware attack using 'stolen NSA cyber-weapon' called EternalBlue sweeps the worlds – and it could get WORSE
June 27, 2017
- NBC News: Paying Off ‘Petya-Variant’ Ransomware Won’t Unlock Your Files
- Microsoft TechNet: New ransomware, old techniques: Petya adds worm capabilities
- Recode: U.S. hospitals have been hit by the global ransomware attack
- Department of Homeland Security, US-CERT: Multiple Petya Ransomware Infections Reported