I’m here to help you avoid the Walk of Shame. You know that walk—the one down the hall to tell someone in IT that you’ve made a huge mistake. After all, you don’t want to be like the poor soul working for the Milwaukee Bucks who released all their employees’ W-2 forms to a hacker who used email spoofing to impersonate the team’s president.
You may not be a high-dollar NBA player, but your inbox is a lucrative target for hackers. They can use you to compromise your association’s members. All they have to do is fool you into clicking a link or opening a file—and that’s not so hard to do with email spoofing.
What you need to know about email spoofing to protect your association
Hackers use email spoofing to phish you. They pretend to be someone they’re not so they can trick you into clicking on a link or opening an attachment. Once you make that huge mistake, they load malware onto your machine.
Here’s how it looks in real life: You receive an email from your colleague Heather—or at least the email looks like it’s from Heather. It shows her email address and name in the ‘From’ fields.
But the strangely written text asks you to review an attachment. Now, you’re wondering, is this email really from Heather? You won’t be able to tell unless you make the effort to view the source code in the email header and check the IP addresses listed in the ‘Received or ‘Return-Path’ fields to make sure they’re legit.
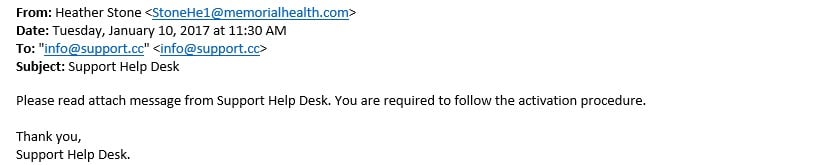
For example, this email appears to be from a ‘legitimate’ address—it’s your colleague Heather asking you to read an attached message from the IT department. Or is it?
- If you open and review the email header, you’d see the actual sender’s domain is not “memorialhealth.com.” That’s the biggest giveaway that something’s phishy here.
- Poor grammar is a telltale sign: “attach message” instead of “the attached message.”
- The ‘To’ address is incorrect—again, not a “memorialhealth.com” email address like you’d expect.
- The request from Heather on behalf of the “Support Help Desk” doesn’t follow the hospital’s usual standard operating procedures.
Unfortunately, all hackers need for email spoofing is access to an email server and email software that allows them to enter spoofed names and email addresses in the ‘From’ fields. Your association can frustrate these efforts by preventing your email addresses from getting spoofed, preventing spoofed emails from entering your staff’s inboxes, and teaching staff how to recognize phishing attempts, like spoofed email addresses.
How to prevent hackers from spoofing your email addresses
One way to prevent hackers from spoofing your email domains is to change your association’s email authentication protocols. For example, to lessen the chance that any emails spoofing our DelCor email addresses will get delivered to other people, we adjusted how our email domains tell other systems to handle incoming messages that appear to be from DelCor. You can do this too by adding two special records to your domain name: SPF and DKIM.
- The SPF (Sender Policy Framework) record is a public list of approved senders. It lets other email servers know whether the sending server is authorized to send email from your domain. If the recipient’s spam filter service is checking the records, the hacker’s message won’t get through because their server isn’t on ‘the list’ of approved senders for your domain. Remember to include any other email services you use on that list, such as your AMS, event registration system, email marketing service, and other systems that send email on your behalf.
- The DKIM (Domain Key Identified Mail) record is harder to explain, but basically involves a comparison of private and public keys generated by your mail server. An email is only accepted by the receiving server if the keys match. The website MXtoolbox.com allows you to check SPF and DKIM records for any domains, including your own.
Now, the problem is, even if you set up SPF and DKIM records for your domain, if the receiving mail systems aren’t performing validation checks, your domain can still get spoofed.
Also, beware hackers who use similar-but-not-quite-right email addresses—for example, something like loretta.delcor.com@gmail.com or loretta@delcor.com.co (notice the extra .co at the end). Spoofing attempts like this would bypass any SPF/DKIM on the delcor.com domain because the spoofed email address uses a different domain—in this example, gmail.com and delcor.com.co, not the legitimate delcor.com. Recipients should know that’s a phishy-looking email address.
Despite these issues outside your control, your IT staff should have the SPF and DKIM authentication methods in place for your sending email domains. If you take these actions, ISPs will consider you a responsible sender and your email deliverability rates will improve in the long-run.
How to prevent spoofed emails from entering your inbox
You can minimize the chances of getting spoofed by making sure you and all your email users receive regular cybersecurity training. You can find self-paced learning tools online. Better yet, talk to your Managed Services Provider (MSP) about training or support they may offer.
Another anti-spoofing tactic we implemented at DelCor was changing how our email filters look at incoming messages. Our server performs checks against incoming emails and blocks those that don’t pass validation tests. Just know there’s a chance you could end up blocking legitimate incoming messages if the senders don’t have their SPF and DKIM records set up correctly.
To prevent becoming the victim of email spoofing, you can’t only rely on your IT department to make these changes. Instead, you must make it your habit to think twice before opening attachments or clicking on links you’re not expecting. If you need to, slow down!
If you’re not sure you’re looking at a legitimate email, get in touch with the person who seems to be asking you to open a document or click on a link. Call them or open up a new separate email and ask them if they just sent you something. Better to take a moment to double-check than make that Walk of Shame.
How else might your association be vulnerable to hackers? Download our infographic, Is Your Organization Protected from Cyberattacks?, to find out.
photo